SUPPLY CHAIN ATTACKS
Threat groups target less secure elements in your supply chain to infiltrate your environment and destroy or exfiltrate trade secrets, proprietary production IP, customer data, and other sensitive data. For enterprises, supply chain attacks are difficult to defend, as any one supplier in your logistics chain, or even a downstream partner, could unknowingly become an entry point for infiltrating your internal network.
USE CASES
From Stuxnet (2010) to SolarWinds (2020), supply chain attacks are perfect examples of the potential damaging capabilities behind 21st-century cyberattacks. Read how CyCraft IR Services identified, contained, and terminated a sophisticated year-long supply chain attack targeting Taiwan’s semiconductor industry.
Failed due diligence investigations during mergers and acquisitions can also lead to business-altering security incidents–such as the 2018 Marriott Starwood data breach, resulting in fines exceeding 100 million dollars. Our customer was about to perform a pre-acquisition due diligence cybersecurity investigation. The client estimated the entire digital forensic investigation would take several months to complete. CyCraft did it in a few days. Not only did CyCraft reduce investigation time by over 99 percent, but cost and workforce-hour investment were further reduced by an estimated 95 percent.
SECURITY MADE F/A/S/T

FAST
RiskINT™ notifies you immediately when a potential threat in your supply chain is detected. Our customers receive comprehensive, actionable reports detailing the possible risk, how to verify the threat step by step, and what security measures need to be deployed.
ACCURATE
RiskINT™ continuously monitors primary global threat intelligence sources and includes our proprietary threat intelligence built from years of frontline experience battling state-sponsored advanced persistent threats (APT). CyCraft’s AI-driven technology–the same technology that defends Taiwan government agencies, critical infrastructure, top financial institutions, and Fortune Global 500 companies with our compromise assessment(CA), incident response (IR), and managed detection and response (MDR) services.
SIMPLE
RiskINT™ reports thoroughly detail the severity of your potential supply chain threat and provide clear, actionable steps that guide you through threat verification and response. Our CyCraft RiskINT™ Services team of expert security analysts is standing by to add any clarity or offer any assistance that you may need.

THOROUGH
Once verified, CyCraft IR Services can contain and eradicate the threat targeting your supply chain. We rescan and confirm eradication with the strict AI-driven vetting process of CyberTotal so that you can get back to business without incident and with confidence.
WHY CYCRAFT?
INDUSTRY RECOGNITION
In the past year, CyCraft outperformed all other MITRE ATT&CK® Evaluation vendors in Technique, Tactic, and General detections with zero configuration changes. CyCraft AIR and CyberTotal both received the Best of Show Grand Prize Award for Security Solutions at Interop Tokyo 2020; CyCraft also received 20+ 2020 Cybersecurity Excellence awards in categories including Managed Detection and Response, Incident Response, Threat Intelligence, and Artificial Intelligence. CyCraft is a proud member of FIRST, a premier organization for incident response security teams.





MITRE ATT&CK Evaluations Validates Industry Leadership for CyCraft AIR Managed Detection and Response. CyCraft AIR scored more real-world GTT detections (General, Tactic, and Technique) than any other vendor solution and with zero configurations.
CYCRAFT
COMMUNITY TESTIMONIALS
“CyCraft has a deep understanding of information security and top-tier technology to prove it.”
Telecommunications, Japan
“CyCraft’s AI-driven managed detection and response, automated forensics, and security visualization showed us the key points and enterprise-wide root cause of all attacks, as well as greatly reduced our investigation time.”
Telecommunications, Taiwan
“CyCraft’s customer support provided excellent communication, incident reports, and response times, leaving us feeling confident and at ease with our security situation. “
Telecommunications, Taiwan
“We were impressed with their innovative technology, such as their intuitive dashboard that made it easy for analysts to analyze and re-analyze intrusion attack data.”
Interop Tokyo 2020, Best of Show Award’s Judge
CYCRAFT
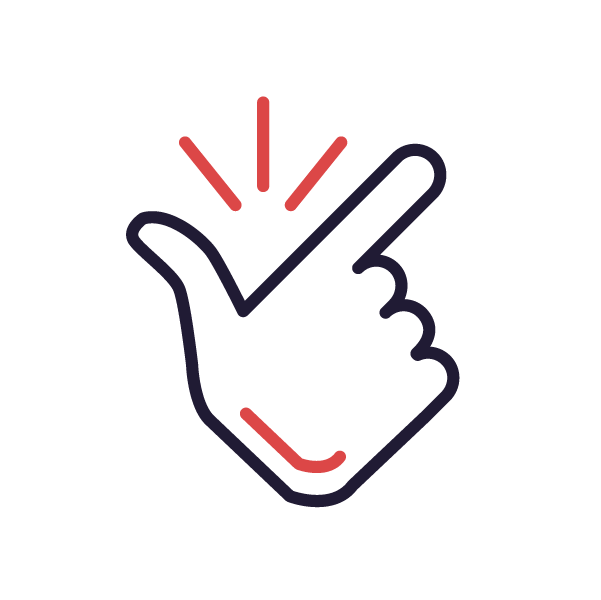
IS TRUSTED BY
Fortune 500
Companies
Financial
Institutions
Law
Enforcement
Government
Agencies
Critical
Infrastructure
Airlines
Manufacturing
Hi-Tech
Telecoms
S0Cs
Many more…
CYCRAFT
IS TRUSTED BY
RELATED RESOURCES
ABOUT CYCRAFT
SERVICES
CyCraft Services provides organizations worldwide with the innovative AI-driven technology necessary to stop cyber threats in the 2020s. The CyCraft AIR platform is uniquely designed to detect the latest trends in malicious behavior, automate investigations, and auto-triage alerts, allowing CyCraft customers to detect, track, contain, and eradicate threats in real-time.
This unique approach empowers CyCraft customers to terminate unauthorized access to their environments faster and prevent intrusions from escalating into business-altering incidents. CyCraft also provides customers with proactive services to improve their visibility, elevate their threat intelligence on threats targeting their industry, hunt down threats, fill in defense gaps, and harden their defenses because everything starts from security.
JOIN THE
CYCRAFT
COMMUNITY
F / A / S / T RESPONSE
FAST | ACCURATE | SIMPLE | THOROUGH
Your CyCraft representative is standing by to help you with an incident or answer any question regarding our incident response, compromise assessment, or managed detection and response services